HackerOne: Using Open Innovation to Foster a Cyber Secure Environment

The world of cybersecurity can be a complex place. With the advent of the internet, increasingly more data is ripe for hacking and companies are scrambling to protect it. HackerOne thinks it has a solution to keep information protected for the long term.
Amongst the many companies taking advantage of the benefits of open innovation, HackerOne has leveraged a community of web hackers to create a leading cybersecurity business that helps the world’s largest companies detect and correct bugs in their respective ecosystems. HackerOne is a bug bounty platform that connects businesses with cybersecurity researchers. It started in 2012 after two Dutch hackers, Michiel Prins and Jobert Abma, made a target list of 100 high-tech companies that they wanted to try to hack. Soon, they had found security vulnerabilities in Facebook, Google, Apple, Microsoft, Twitter and 95 other companies’ systems.[1] Ultimately Sheryl Sandberg of Facebook raised this issue to Facebook’s then CIO who paid the two hackers $4,000 for their find, and HackerOne was born.
Why Open Innovation?
Prins and Abma struck gold at the right time with the advent of open innovation and the growth of Uber, 2012 was a perfect inflection point of open innovation and the gig economy to make HackerOne thrive. The open bounty program that this platform uses is a great way to allow researchers to help companies be safer, while keeping these researchers free from potential recourse from the government. As stated by former Facebook CIO Alex Rice
“If researchers find something, they don’t know if they’ll be welcomed with open arms or delivered to the FBI kicking in their door. There’s a long stream of people with good intentions being treated very poorly as a result of that work.”[2]
HackerOne allows researchers to essentially contract out their services to large corporations while maintaining their distance and staying out of potential legal trouble. This platform opens the opportunity for researchers to do good with bugs they find and get paid by corporations as opposed to selling information to the dark web. HackerOne takes a 20% fee from the bounty corporations pay for playing the “middleman”.
How HackerOne’s bounty program works [3]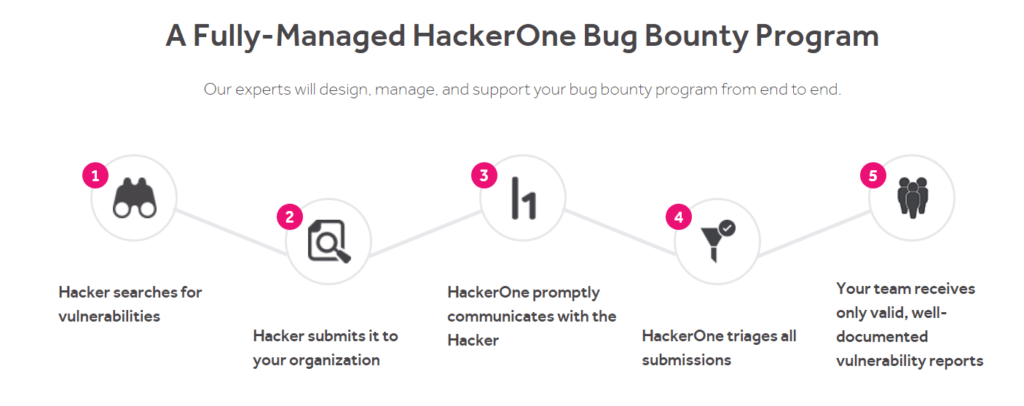
How HackerOne’s bounty program works [3]
How to Scale
Since its founding, HackerOne has been on a tear, gaining notoriety from many Fortune 500 companies. Facebook, Uber, Google, and Coinbase are just a few of the companies that have current partnerships. Recently, General Motors has decided to extend a 2016 program that they had started with HackerOne. As part of the program, GM committed not to sue security researchers for hacking their products, provided the researchers complied with a number of stipulations, such as not disclosing the vulnerability until GM rolled out a solution.[4] GM President Dan Ammann says
“GM plans to offer a cash payment for each “bug” found in this new Bug Bounty program. We’ll show them the products, programs and systems for which we plan to establish these Bug Bounties,” Ammann said. “Then we’ll put them in a comfortable environment — ply them with pizza and Red Bull or whatever they might need — and turn them loose.”[3]
In their efforts to push open source cyber security forward, HackerOne has even gotten the attention of the US government. Ash Cartrer, Secretary of Defense notes
“We know that state-sponsored actors and black-hat hackers want to challenge and exploit our networks. We know that. What we didn’t fully appreciate before this pilot was how many white-hat hackers there are who want to make a difference, who want to help keep our people and our nation safer.”[5]
What’s Next?
As competition continues to heat up in the space, HackerOne must continue to innovate. One area that may be low hanging fruit is education. Most hackers are self-taught, so it remains to be seen how formal education will impact the space. HackerOne has room to provide formal education and help young hackers self-learn as much as possible. HackerOne is currently broadening its researcher base to get more top hackers. This is a priority, and the company is experimenting with different solutions to the challenge. There is the Hacker101.com site with tutorials, blog posts, HackerOne sponsored answers on Quora, and they work with some universities on their cybersecurity courses to enable them to train people.[5] Another space that may be ripe for HackerOne is personal computing. All computers will ultimately have a vulnerability. Can HackerOne grow its base of hackers wide enough to help patch up the vulnerabilities all of us have as common day to day users of the internet? Should that be feasible, there is a large pool of demand waiting for HackerOne to expand.
Sustainability
As we look further into the future one can only wonder about the sustainability of this model. The bounty program feels eerily similar to Uber’s contract model, and it begs the question of will the government ultimately step in and claim that these cybersecurity researchers are not contractors but are instead employees that have the rights to benefits? Will HackerOne need to look at bringing more expertise in house?
(Word count: 785)
[1] “HackerOne connects hackers with companies and hopes for a win-win.” The New York Times, June,7th 2015. https://www.nytimes.com/2015/06/08/technology/hackerone-connects-hackers-with-companies-and-hopes-for-a-win-win.html?_r=0
[2] “HackerOne emerges with $9 million to root out software bugs.” The Wall Street Journal, May, 28th 2014. https://blogs.wsj.com/venturecapital/2014/05/28/hackerone-emerges-with-9-million-to-root-out-software-bugs/
[3] Image source: HackerOne company website, https://www.hackerone.com/product/bounty, Accessed November 11th, 2018.
[4] “General Motors doubles down on bug bounty cybersecurity effort.” Forbes.com, August 5th, 2018. https://www.forbes.com/sites/davidsilver/2018/08/05/general-motors-doubles-down-on-bug-bounty-cybersecurity-effort/#4764496bf33e
[5] “Hack the Pentagon.” https://www.hackerone.com/resources/hack-the-pentagon , Accessed November 12th, 2018
[6] “Hacker education inclusivity and shifting perception of bug bounties.” The Daily Swig Web Security Digest, November 7th, 2018. https://portswigger.net/daily-swig/hacker-education-inclusivity-and-shifting-perceptions-of-bug-bounties



I think that your question around bringing hackers in-house or considering them employees is an interesting one. I would think hackers would prefer to work on a consultative basis given the counter-culture nature of the community, but perhaps this is only because those jobs do not currently exist.
One concern I have around encouraging hackers to penetrate systems is the safety of information. While there may be some ‘white hats’ out there that are willing to test systems purely for sport/testing, I would be concerned that these challenges invite malicious actors who may use the information they find.
I think that if this business scales and becomes relevant for the society, the employment state of the hackers (contractors vs full time employees) will spark a lot of debate. This is not only because of the accounting standards that each country may employs but, perhaps more importantly, due to responsibility issues. Hackers get exposed to very confidential information and the big question here is who is currently responsible for any information leak, the hackers or HackerOne? Ultimately, I think both should be held accountable and thus a more formal employment relationship (i.e. full-time employees) should be formed.
Further building on the above, I would like to express my moral concerns regarding the business model. Is it okay to encourage individuals to access confidential information of companies and of consumers’ personal data? Even if hackers have good intentions, is it completely safe to help them acquire data that can lead to significant financial returns to them if exploited unethically?
Another database could be created with all the cases of the bugs that the hackers have helped identified. This database could be sold to major corporations under a subscription model which could generate additional revenue for HackerOne to support their other cyber-security initiatives (or to reduce the 20% fees)
I’m very impressed by HackerOne’s business model, as it essentially created a legal platform and a market for hacker activities. Your point about the education space as a next step for HackerOne is particularly interesting. On one hand, it increases the supply of the platform contributors, and further builds the credibility of the platform’s expertise. The partnership with universities is a brilliant idea. I can even picture a similar model to Kaggle for machine learning problems, where students may work on real company vulnerabilities for their coursework, which increases HackerOne’s supply of researchers, and at the same time trains the students. However, I’d like to see more control systems from HackerOne to prevent malicious actors to abuse the hacking knowledge they learned. For example, if a hacker found a particularly lucrative vulnerability, what’s to stop the hacker from profiting from that vs. getting paid by the company? Should the hackers violate the rules, are they registered in a way that can be identifiable?
A friend once told me, “there are two kinds of companies. A company that has been hacked and a company that does not know they have been hacked.” The risk of cyber attack is a universal business problem in the 21st century. HackerOne’s product sounds like an incredibly creative and effective way to mitigate this risk. While I’m worried about the contractor v. employee debate as well, I’m more worried about HackerOne’s ability to attract and retain hackers through an open innovation model. Open innovation is key to their success but as the trend continues to grow and expand into other industries, it will be imperative for HackerOne to develop strategies to stay competitive in the gig labor market.
I think the comparison to Uber’s business model is very accurate! My lovely home state of California currently has the strictest regulations in the US surrounding gig economy labor. A recent ruling stated that to be considered and independent contractor you must pass 3 tests: “One, that the contractor provides the service free from the company’s control; two, that the service provided is outside the company’s core business, such as a janitor at a law firm; and three, that the contractor is an independent professional engaged in providing their service to companies other than the one in question.” Under these restrictions, I do think that ultimately the hacker will have to be considered an employee, but we will have to see if other state/federal laws follow in California’s suit. I do not believe that the hackers are being taken advantage of in this situations, as it appears HackerOne has given them a great way to legally monetize their skills, so I would hope that the current business model is allowed to continue.
source: https://money.cnn.com/2018/05/01/news/economy/california-gig-employer-ruling/index.html
My greatest concern in all this industry is data safety. I believe that many high-skill professionals of this field won’t disclose identity to anybody, including HackerOne. Thereby, there will be no safeguard against the selling of information about vulnerability to a number of parties.
Thereby they will become rather a consulting company – a collection of IT-professional devoted themselves to legal hacking. Which is not bad after all.
This is a really interesting company, great post! This notion of “helpful hackers” is a really innovative ideas, and given it seems like the company is just matching supply and demand between hackers and companies in need of their services, I don’t see why they should be classified differently from Uber drivers. Further, I echo some of the concerns in the comments around data safety. Given this service is appealing to hackers who are taking a risk, I believe it is in everyone’s best interest to keep their identities anonymous as they carry out a new form of “vigilante justice”
Fascinating topic and great article. I do think that HackerOne needs to bring on more expertise to establish the company and move beyond being a community of well-intentioned hackers to a viable business has mass appeal to companies across many industries. The experts I would look to hire would be a community manager to keep hackers engaged and recruit the best talent, subject matter experts in cyber security to objectively evaluate the hacker community, and some senior sales individuals with business expertise that can relate to the concerns of business leaders and can pitch HackerOne as a solution to those needs.