Ghosts in the power machine

Digitizing the electricity supply chain opens opportunities… but also vulnerabilities – how are manufacturers responding?
Growing digital, growing vulnerable
Turning the lights on means much more than flipping a switch these days. With the growing digitization of power infrastructure, supplying electricity entails an entire ecosystem of sensors, controls, and data management systems that are increasingly inseparable from the traditional supply chain, spanning from power generation, to transmission and distribution, to the end-customer.
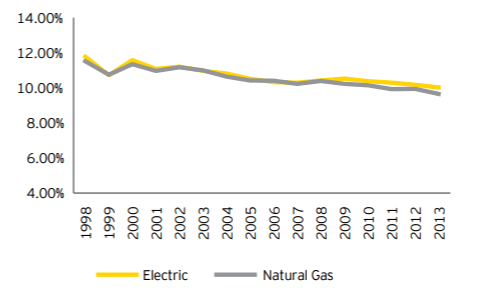
In part, a continuing decline in returns have prompted this move to digital. Established players in the electricity sector have seen their earnings suffer from increasing deregulation and new entrants (see Figure 1). Coal-powered generators are facing cost pressure from cheaper gas and renewable sources, while those renewables are in turn coping with wind and sun sources whose output is harder to predict than traditional “base load” generation. No surprise then that companies are attracted to the digital approach, when “going digital” has the potential to improve utility earnings by 7% in generation alone, and 20-30% across the value chain. [1] Digitization has enabled power companies to amass an incredible wealth of data, improve productivity and efficiency, and engineer more efficient and responsive technologies.
However, vulnerabilities have emerged as fast as digitization has spread across the electricity supply chain. The capabilities to collect data and act on it remotely yield new opportunities for malevolent actors to disrupt operations. In 2015, a malware called Black Energy interrupted Ukraine’s power grid by infiltrating a utility company’s systems and cutting off efforts to repair them. [2] Future attacks could put more at risk by compromising more critical communication links or targeting physical facilities directly, rather than their surrounding systems. [3] The advent of digital supply chains therefore raises growing concerns of security and stability that operators must contend with more frequently.
Figure 1: Allowed returns (ROE) for regulated electric
and gas utilities in the US, 1998-2013
Ghosts in the generation machines
Enter equipment manufacturers, who emerge as part of the frontline in defending from digital intrusions. One notable example, General Electric is building on technologies already embedded in its power generation turbines to add defensive capabilities to their customers’ supply chains. GE used its existing Digital Twin platform to produce a defensive one called Digital Ghost. [5] A digital twin is a virtual model of a physical equipment that collects data and predicts outcomes, improving the machine’s life and performance. [6] Similarly, GE’s Digital Ghost simulates the physical machine and uses accumulated performance data to detect anomalies and correct them without human intervention.
The Digital Ghost approach follows three phases – problem detection, location, and neutralization. [7] For example, a turbine producing anomalous power fluctuations triggers the resident “ghost” system, which compares the output to benchmarks for that specific turbine. The system then isolates the problem and takes the corrective measures (e.g., shut-down, flag for human follow-up) to resolve the threat. The speed at which the turbines operate advantages a digital approach; gas turbines adjust every 40 milliseconds, exceeding the pace of human operator intervention.
GE will roll out the Digital Ghost feature in phases. [8] The first in 2018 will enable equipment to identify and locate threats. The second phase in 2019 will finalize the capability to resolve issues. The overall effort focuses on gas and steam turbines, older and more established technologies with a large body of existing performance data and benchmarks.
Powering expansion, exploring adjacencies
Looking at next moves in the medium term, GE could apply this Digital Ghost to other sub-sectors within electricity (e.g., wind turbines) as well as more extensively along the supply chain, collaborating with manufacturers of grid and other equipment. The same capabilities that currently allow systems to talk across generation, transmission, distribution, and the end-customer’s business or home could also collaborate to identify threats and coordinate responses across the supply chain. For example, an attack on grid management software could trigger that asset’s “ghost” to curtail production at the plant level, while signaling downstream storage sources to provide alternative supplies during the interruption.
Moreover, such supply chain security improvements are not limited to the power sector. GE should explore this Digital Ghost approach to other data-rich, automated, and capital-intensive activities. Aviation, oil and gas, and medical systems exemplify some other, similar spaces. [9] Critical systems in urban infrastructure or industrial processes could benefit from built-in controls that already use the stream of data to triage interventions, acting when human decision-making could lag.
What’s next?
Much like digital transformations overall, securing such systems is an industry changer. However, GE will face design and implementation choices before it can scale. How much should it invest in interoperability of the Digital Ghost approach with other stakeholders’ asset? How can this be scaled, regardless of the underlying “hardware”? So far, the success of Digital Ghost has grown from a customized, system-specific approach. The greater value, however, lies in optimizing the entire supply chain from generation to distribution, but herding a group of ghosts is no easy task.
(798 words)
[1] Adrian Booth, Niko Mohr, and Peter Peters, “The digital utility: New opportunities and challenges,” McKinsey, May 2016, https://www.mckinsey.com/industries/electric-power-and-natural-gas/our-insights/the-digital-utility-new-opportunities-and-challenges, accessed November 2017.
[2] Supervisory control and data acquisition. Chris Vallance, “Ukraine cyber-attacks ‘could happen to UK’,” BBC, February 29, 2016. http://www.bbc.com/news/technology-35686493, accessed November 2017.
[3] Robert M. Lee, Michael J. Assante, Tim Conway, “Analysis of the Cyber Attack on the Ukrainian Power Grid,” E-ISAC Defense Use Case, 2016, https://ics.sans.org/media/E-ISAC_SANS_Ukraine_DUC_5.pdf, accessed November 2017.
[4] Matt Rennie, “Capital outlook: power and utilities,” 2014. http://www.ey.com/Publication/vwLUAssets/ey-capital-outlook-power-and-utilities-article/$FILE/ey-capital-outlook-power-and-utilities.pdf, accessed November 2017.
[5] Diarmaid Williams, “GE attempts to make power plants immune to cyber threat,” Power Engineering International, August 29, 2017. http://www.powerengineeringint.com/articles/2017/08/ge-attempts-to-make-power-plants-immune-to-cyber-threat.html, accessed November 2017.
[6] GE Digital Twin, From GE website, https://www.ge.com/digital/sites/default/files/Digital-Twin-for-the-digital-power-plant-.pdf, accessed November 2017.
[7] Williams, Power Engineering International.
[8] Ibid.
[9] Larry Dignan, “GE aims to replicate Digital Twin success with security-focused Digital Ghost,” ZDNet, March 24, 2017, http://www.zdnet.com/article/ge-aims-to-replicate-digital-twin-success-with-security-focused-digital-ghost/, accessed November 2017.



If I were in charge of the GE Digital Ghost program, I would not immediately focus on interoperability with my customer’s other assets. The assets that Digital Ghost would operate on are already integrated into the customer’s system, and the customer likely has some type of control system in place to account for factors such as reduced wind (in the case of a turbine). The value of Digital Ghost is that GE has accumulated a treasure trove of data on its own products, which can then be used to detect future abnormalities in the behavior of these products due to some kind of cyber attack. [1] Integrating Digital Ghost with non-GE assets may not be able to provide the same type of advantages to the customer, since GE doesn’t have significant historical data on the proper functionality of these assets, and it seems unlikely that the other manufactures would want to share this data.
Regardless, I believe that GE has the opportunity to develop a new infrastructure software security group. It seems that their approach to detecting potential hacks is quite revolutionary, and could be monetized. Once again, however, GE would have to gain access to historical data on the performance of non-GE assets. If companies or manufacturers were willing to share this data with GE (even for a price), I can’t see any barriers to GE developing a robust infrastructure security group that functions along the entire supply chain. However, whether GE wants to move into a SAS company is a question best left for John Flannery.
[1] Govtech.com. (2017). GE Teaches Electric Power Plants to Self-React to Computer Hacks. [online] Available at: http://www.govtech.com/security/New-GE-.html [Accessed 26 Nov. 2017].
The GE Digital Ghost is fascinating technology! I believe GE should focus on applications in additional industries, namely because of the self-correcting feature. Given the appropriate contract terms, I would expect companies to share data for installation of this technology to ensure the safe operation of equipment. In my experience with the oil and gas industry, control devices are restricted to hardwired connectivity due to the susceptibility of wireless technologies to digital intrusion. If this technology could be proven to work effectively and reliably, with minimal maintenance required by GE, I believe the oil and gas industry would adopt it to capture additional technological efficiencies. I am most concerned with how GE will demonstrate the Digital Ghost effectiveness to capture the early adopters in other industries. Industries, especially in the industrial sector, are skeptical of new technology and slow to adoption due to the high consequences if something should go wrong.