SimpliSafe- Home Security Solutions in a Digital World

The digital transformation gave rise to SimpliSafe, a startup in the home security space targeting renters. As has happened to many Internet of Things companies, the very technology that gave birth to SimpliSafe is now threatening its existence.
Home Security Market: Expanding Beyond Rich Homeowners in Safe Neighborhoods
For decades, big alarm monitoring companies such as ADT have dominated the home security market by offering huge upfront savings on professional alarm installation and then charging high fees as part of a multiyear contract for professional monitoring services. Due to the necessity of installing equipment, the high cost of monitoring, and the long-term contracts, wealthy homeowners historically represented the overwhelming majority of home security customers. Meanwhile, the alarm companies completely ignored young, lower income renters living in less safe neighborhoods. This inconsistency led to the 2006 founding of SimpliSafe, a company looking to capture the rental security system market with new technology and a new business model.
SimpliSafe’s founder, Chad Laurans, a Harvard graduate, first decided to attack the home security market after burglars robbed several of his friend’s apartments while they were in college [1]. He looked at the $17.5bn in 2006 home security sales [2] and the fact that approximately 37% [3] of Americans rented their homes and saw an opportunity to apply new technology to a stodgy industry.
A New Business Model Emerges
SimpliSafe’s competitive advantage stems from the ease of installing a wireless system using adhesive tape and then easily transporting the system upon moving. Unlike traditional players, SimpliSafe charges full price upfront for equipment (starting at $230) that is easy to install and then charges more reasonable fees ($15/month and no contract) for professional monthly monitoring [4].
The equipment consists of a series of different types of sensors connected via a wireless network and a command center that links to professional monitoring services through a provided cellular link. The product resonates even more with its target audience by not requiring a landline, something many Millennials have never had as adults. Customers can easily add or subtract sensors to the system and the sensors have different functions, such as motion detection, glass breakage, and smoke detection. Upgrading to a higher monitoring service for $25/month allows customers to remotely program the alarm using a cell phone.
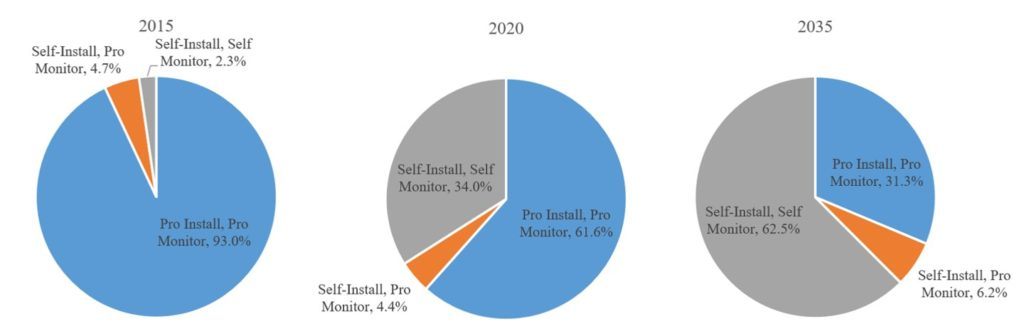
Figure 1. Market share for self-installed alarm systems, such as SimpliSafe’s, is expected to grow significantly over the next 20 years [5]
A Chink in the SimpliSafe Armor- Threats to the Internet of Things
Security researcher Andrew Zonenberg rocked SimpliSafe’s world in February 2016 by publishing a blog post detailing how a person with a second SimpliSafe system, a microcontroller board, and rudimentary coding skills could bypass the SimpliSafe system [6]. The equipment, purchased for $250, combined with C Language code, allowed him to capture the frequency used to disarm the alarm system and then parrot it back using his equipment (could be replicated with equipment valued at $50) [7]. Unfortunately for SimpliSafe, multiple mainstream media sources picked up the story, delivering a strong reputational blow to the company.
It turns out that SimpliSafe is not the only security system to succumb to this threat as ADT was also caught using unencrypted signals in its wireless offering [7]. While the Internet of Things presents many enticing opportunities, it also makes all involved systems vulnerable to hacking attacks.
Figure 2. Equipment used by Andrew Zonenberg to hack SimpliSafe’s alarm system [6]
Fixing the System
SimpliSafe’s response to this threat was weak at best. The company posted a blog article dismissing Zonenberg’s findings as unrealistic and pointing out all the ways in which SimpliSafe is immune to traditional burglar’s methods that were completely unrelated to Zonenberg’s claims [8]. This tone-deaf response didn’t address SimpliSafe’s fatal flaw- the company failed to design its hardware to receive routine firmware updates. Consequently, the company is unable to provide a software update and is virtually helpless to solve the problem.
As companies continue to innovate in the digital transformation space, they must ensure that they can continually update their products with software patches. Companies like Tesla are already doing this, allowing existing owners to benefit from software updates [9].
SimpliSafe should respond by sending each of its current subscribers a USB flash drive loaded with firmware to address the security threat. Like other Internet of Things providers, SimpliSafe should design future hardware to allow wireless software updates that can address new threats. While this post points to a specific issue at a small company, all Internet of Things companies will have to harden their defenses against bad actors.
(720 words)
Sources
[1] New England Venture Capital Association, “Meet the NEVYs Nominees: Entrepreneur of the Year, Tech, http://www.newenglandvc.org/meet-the-nevys-nominees-entrepreneur-of-the-year-tech, accessed November 2016.
[2] IBIS World, “Security Alarm Services Profile,” http://clients1.ibisworld.com/reports/us/ industry/keystatistics.aspx?entid=1491, accessed November 2016.
[3] National Multifamily Housing Culture, “Quick Facts: Residential Demographics,” http://www.nmhc.org/Content.aspx?id=4708, accessed November 2016.
[4] SimpliSafe, http://www.simplisafe.com, accessed November 2016.
[5] Bob Bryan, “Silicon Valley Will Soon Become a Massive Player in Home Security,” Business Insider, http://www.businessinsider.com/self-monitored-home-security-systems-market-share-2015-7, accessed November 2016.
[6] Rafi Letzter, “There’s a Major Unfixable Flaw in a Security System Used in Over 200,000 Homes,” Business Insider, http://www.businessinsider.com/simplisafe-security-system-hack-2016-2, accessed November 2016.
[7] Thomas Fox-Brewster, “300,000 American Homes Vulnerable to Hacks of ‘Unfixable’ SimpliSafe Alarm,” Forbes, http://www.forbes.com/sites/thomasbrewster/2016/02/17/ simplisafe-alarm-attacks/#2495dde579a3, accessed November 2016.
[8] “Our Commitment to Your Security,” http://simplisafe.com/forum/customer-support-forum/installing-and-using-simplisafe/our-commitment-to-your-securi, accessed November 2016.
[9] Tesla Software Updates, https://www.tesla.com/support/software-updates, accessed November 2016.
Cover photo from www.simplisafe.com
Note: The author gained much of the knowledge provided in this blog post as a former customer.




SimpliSafe certainly put themselves in a tough bind with the hardware they created that could not be updated remotely. I wonder if their lack of response came from a small or non-existent drop in customers as a result of this discovery. While it seems like it’s not too difficult to disarm the SimpliSafe using the hack, I wonder if just having the SimpliSafe acts as enough of a deterrent to cause burglers to go elsewhere.
Great post AJ.
This post raises an interesting challenge regarding IoT and digital devices in general. Companies constantly increase the flow of information of connected devices in order to improve functionality and ease of use. However, doing so also substantially increases user privacy threats and cyber-security threats. It is much easier hacking into a wireless system compared with a closed-loop, wired one. Personally, I think a more conservative approach is needed when dealing with security and safety systems. Stand-alone systems are less convenient, but are safest in terms of cyber-security because to hack them you need to approach them physically. In this case, I am not sure about the suggestion to design future hardware to allow wireless software updates. I think it will provide another “entry point” for hackers with fake updates to bypass the SimpliSafe system.
Home Security is an issue a lot of people are concerned about these days and it seems like SimpliSafe is a great option. My concern with the product involves data connections. Even if the SimpliSafe is using a cell link, it seems like the system would be vulnerable to electronic jamming, so a hacker wouldn’t necessarily need to know specific frequencies to jam the signal.
This is a very strong industry and many people are transitioning to digital to protect their homes. It is hard for consumers to understand the edge one product has over the other. SimpliSafe has many competitors, such as Canary, Moni, and traditional home secruity companies with new technology, and it will be interesting to see which products end up with a large portion of market share.