Machine Learning in Cybersecurity: CyberArk
Exploring the role of machine learning in improving cyber defenses in Privileged Account Management
Machine Learning in Cybersecurity: CyberArk
Eric Levine
11/13/2018
Cyberark is an Israeli cybersecurity company that specializes in Privileged Account Management. Among their customers are 50% of the Global Fortune 100 [1]. CyberArk helps to protect organizations from external actors who have acquired insider credentials, and malicious insiders themselves [1]. In both instances, attacks have penetrated the perimeter of an organization. Cyberark helps organizations construct the design of a castle such that the most critical pieces of information are housed within multiple sets of walls. They also help organizations with the systems and processes – like guard patrols – to catch bad behavior early. Cyberark locks up and encrypts credentials in “digital vaults.”
Cyberark helps companies navigate the tradeoff between convenience and security. The more people with local “admin rights” to install software, malware, add users, etc, the riskier the status of the organization. Cyberark’s traditional value prop was focused in laying out the architectural infrastructure maximize these tradeoffs.
Machine learning comes into play in using analysis to detect cyber threats and zero-day attacks (industry lingo for right away) automatically. You can use machine learning to monitor behavior like a referee of a soccer game. Because there are so many simultaneous “players” generating vast amounts of data simultaneously, machine learning is paramount to learning what sort of behavior is normal vs. risky. With this backstop in place, an organization can allow more users convenient access, with the capability to identify immediately when an employee or attacker with stolen credentials is behaving in a very strange manner.
An example will help illustrate. Edward Snowden was a malicious insider. He managed to download NSA documents as an inside contractor and leak confidential documents. Had the NSA used machine learning protections, their algorithms would have identified that Snowden was engaging in very unusual behavior on endpoints in downloading a massive amount of data unrelated to his assigned work. The algorithm would have flagged this right away, and perhaps automatically revoked Snowden’s credentials and thus his ability to access the network.
Cyberark is continuing to evolve its offering to keep up with the bad guys. Learning what behavior is “normal” vs. abnormal requires monitoring thousands of employees, sifting through millions and millions of bytes of data, and “knowing” what type of behavior is abnormal and riskiest is also a prediction challenge best suited for machine learning. As the company expands its client base and coverage, the algorithms will improve over time.
In the short term, Cyberark is further building out the capabilities of its machine learning algorithms to identify threats. It has made several acquisitions in the space over the past few years, including (1) CyberIntel, which specializes in threat detection (2) Viewfinity, which simplifies the processes involved in privilege management (better suited for smaller customers). [2 and 3]
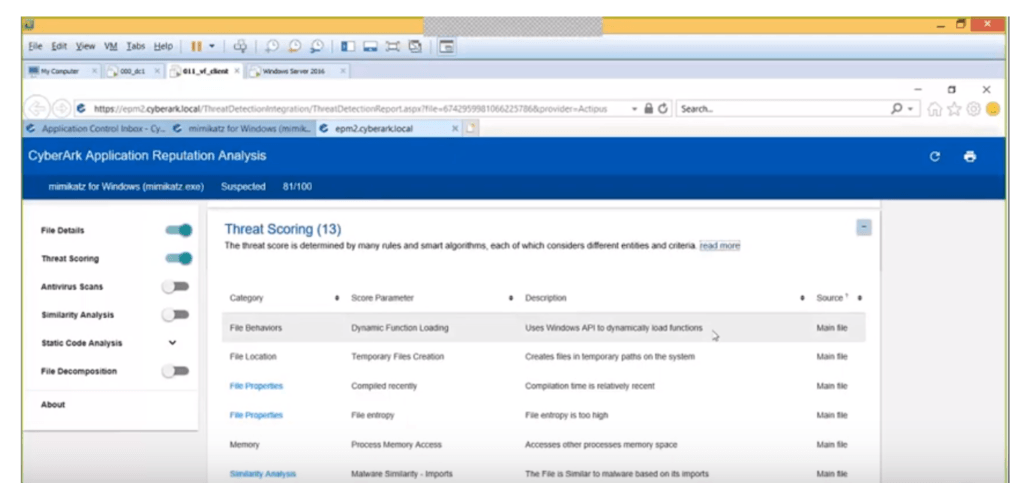
Currently, Cyberark uses 13 different indicators to help “score” threats [Exhibit 1] [4]. They must continue to build out their threat scoring capabilities – improving accuracy and updating the indicators as the bad guys evolve – to improve the accuracy and adapt to a dynamically changing enemy.
The future of IT security is that the volume of applications and other software programs is exploding exponentially, as the process of developing and deploying software is getting much faster thanks to the cloud and an increasingly available off-the-shelf toolbox that can be used by developers. CyberArk should continue to focus its R&D and acquisitions on protecting not just against individuals, but against managing software applications and machines. The future of hacking will increasingly come from attacking machines who improve via machine learning by predicting what techniques are most efficient and effective at evading attention.
Their latest major acquisition in March 2017 of Conjur ($42M) hints at where the future is heading and is a step in the right direction. Conjur provides software that automates tasks in managing machine identities, and managing connections between machines [5]. But Cyberark needs to be investing more in this area to defend against the sophisticated attacks of tomorrow.
One more radical idea would be to hire reformed ex-hackers (ideally from the Israeli / US military so that they can be trusted) to get into the mind of the criminals, test and build out more solutions.
As companies prepare for a world in which attacks are enhanced by machine learning and carried out by machines, and the defenses are provided by machines, what are the risks that the arms race of cybersecurity will accelerate out of our control? From a societal standpoint, is investing more and more in defenses creating stronger and more sophisticated attackers? A parallel would be the way that antibiotics lead to stronger diseases, forcing the entire human population into an arms race against bacteria. What role should regulation play in this arms race?
(774 words)
Bibliography
1. “Cyberark September Investor Presentation.” Cyberark Investor Relations. 11/12/2018.
https://s22.q4cdn.com/395203516/files/doc_presentations/2018/cyberark-investor-deck_sept-2018.pdf
2. “Cybertinel acquired by CyberArk Software.” Crunchbase. 11/11/2018. https://www.crunchbase.com/acquisition/cyber-ark-software-acquires-cybertinel–4d1e30b3
3. “Cyberark Completes Acquisition of Viewfinity, Inc.” Cyberark Website. 11/11/2018. https://www.cyberark.com/press/cyberark-completes-acquisition-of-viewfinity-inc/
4. “Webinar: Machine Learning Prevents Privilege Attacks at the Endpoint.” Viewed 11/13/2018.
https://www.cyberark.com/blog/resource-type/webinar/page/2/
5. “Conjur, Inc. Acquired by Cyberark Software.” Crunchbase. 11/11/2018. https://www.crunchbase.com/acquisition/cyber-ark-software-acquires-conjur–d920145b#section-locked-marketplace
6. “CyberArk Investor Calls for Q4’17 – Q3’18.” S&P Capital IQ.
7. “Pass the Hash.” CyberArk Website. 11/11/2018.
https://lp.cyberark.com/rs/316-CZP-275/images/sb-Pass-the-Hash-05-2018.pdf



While exploring the questions posed at the end of this post, I cannot help but think of the dichotomy between exploitation and exploration in product development. The example suggested above lives in the land of exploitation, where each incremental improvement championed by the ‘defense’ machine is countered by an improvement from the attacker that renders the defense’s improvement useless. Where, then, does exploration factor in? One possibility is that humans could out-explore the machines, even as machines out-exploit humans (and other machines) – basically, once the attacking machine has outmaneuvered (or, better yet, out-exploited) the ‘defense’ machine, human intervention could make a more wholesale change that requires the attacking machine to recalibrate, thereby regaining the upper hand. Of course, the vicious cycle of machine-outsmarting-machine would then begin anew, raising legitimate questions of the long-term viability of the human intervention strategy suggested above.
Eric, I found this fascinating, particularly your suggestion that CyberArk could hire ex hackers to better defend against sophisticated attacks. This is such an interesting proposition, particularly since when it comes to penetrating cyber defenses, it does seem that the hackers have the upper hand, at least for now. I wonder how this would work in practice, since I would imagine that government agencies would be loathe to hire people with criminal records, not to mention that in order to start working for the ‘good guys’ the hackers would first have to be caught. This raises another question – is hacker identification currently a part of CyberArk’s threat detection? As cyberattacks become more frequent and more sophisticated, it would seem to me that we need to be investing in not just detecting threats, but tracing them.
Eric, this is fascinating, particularly your suggestion that we could use former offenders as a kind of crack team of hacker thwarters. This is a very intriguing idea, since it seems that for now at least, the hackers have the upper hand in the fight between the ‘bad guys’ and the ‘good guys,’ frequently escaping detection until they have achieved their malicious purpose. The idea does beg the question of how this would work in practice. It would require us to catch offenders and convince them to work for their captors. This made me wonder whether cyberark’s current detection technology is capable of tracing the source of a hack. I would think that as hackers become more sophisticated and their attacks more frequent, identifying them becomes as important as detecting breaches.
Eric, thank you for expounding on this topic. Cybersecurity is a popular buzz word but I feel like we rarely dive deeper to understand what the real mechanisms or issues are surrounding the topic. I fully agree with what you said about the insider threat, but I am curious if machine learning can be used to stop an outside threat that has already managed to find a way to tunnel in because of a fault in the code. Would AI be able to find this vulnerability too, or are there several more steps required to raise it to this level of sophistication?